概要
MicroMDMで構成プロファイルをインストールしてみたい
前提
ドメイン
mdm.ryuouen.link
サーバ
EC2(Amazon Linux2)
MDM
https://github.com/micromdm/micromdm/archive/refs/tags/v1.10.1.zip
MDMの証明書
https://mdmcert.download/registration
Apple Push Certificates Portal
証明書を取得
- MDMCert
登録情報を設定


メールを受信して認証する

EC2サーバを配備して、MicroMDMのビルドに必要なものを取得
sudo yum install git golang
MicroMDMをダウンロードする
$ mkdir -p micromdm $ cd micromdm/ $ wget https://github.com/micromdm/micromdm/archive/refs/tags/v1.10.1.zip $ unzip v1.10.1.zip $ cd micromdm-1.10.1/
ビルド
make
ダウンロードコマンド実行
$ build/linux/mdmctl mdmcert.download -new -email=hoge@example.jp(認証したメールアドレス) Request successfully sent to mdmcert.download. Your CSR should now be signed. Check your email for next steps. Then use the -decrypt option to extract the CSR request which will then be uploaded to Apple. $
メールに添付された証明書を取得する
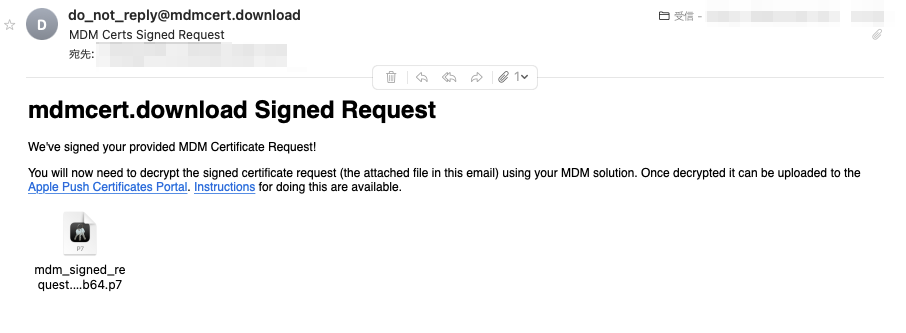
scp mdm_signed_request.20231018_060844_1899.plist.b64.p7 ec2-user@hogehoge(ホスト名またはIP):~/micromdm/micromdm-1.10.1/.
「mdmcert.download.push.csr」を取得
build/darwin/mdmctl mdmcert.download -decrypt=mdm_signed_request.20231018_060844_1899.plist.b64.p7 $ ls -la mdmcert* -rw-rw-r-- 1 ec2-user ec2-user 1127 10月 18 13:09 mdmcert.download.pki.crt -rwx------ 1 ec2-user ec2-user 1679 10月 18 13:09 mdmcert.download.pki.key -rw------- 1 ec2-user ec2-user 964 10月 18 13:09 mdmcert.download.push.csr -rwx------ 1 ec2-user ec2-user 1679 10月 18 13:09 mdmcert.download.push.key -rw-rw-r-- 1 ec2-user ec2-user 9366 10月 18 13:22 mdmcert.download.push.req $
ローカルへダウンロード
scp ec2-user@hoge(ホストまたはIP):/home/ec2-user/micromdm/micromdm-1.10.1/mdmcert.download.push.req .
Apple Push Certificates Portal
https://idmsa.apple.com/IDMSWebAuth/signin?appIdKey=3fbfc9ad8dfedeb78be1d37f6458e72adc3160d1ad5b323a9e5c5eb2f8e7e3e2&rv=2
新規登録
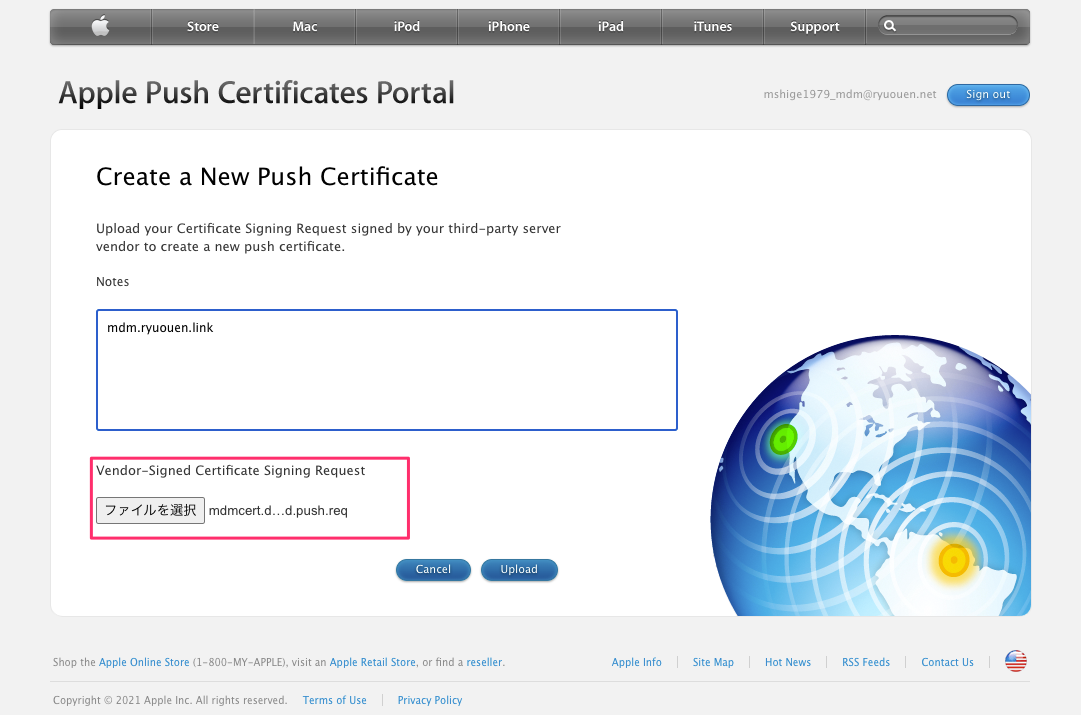
ダウンロード
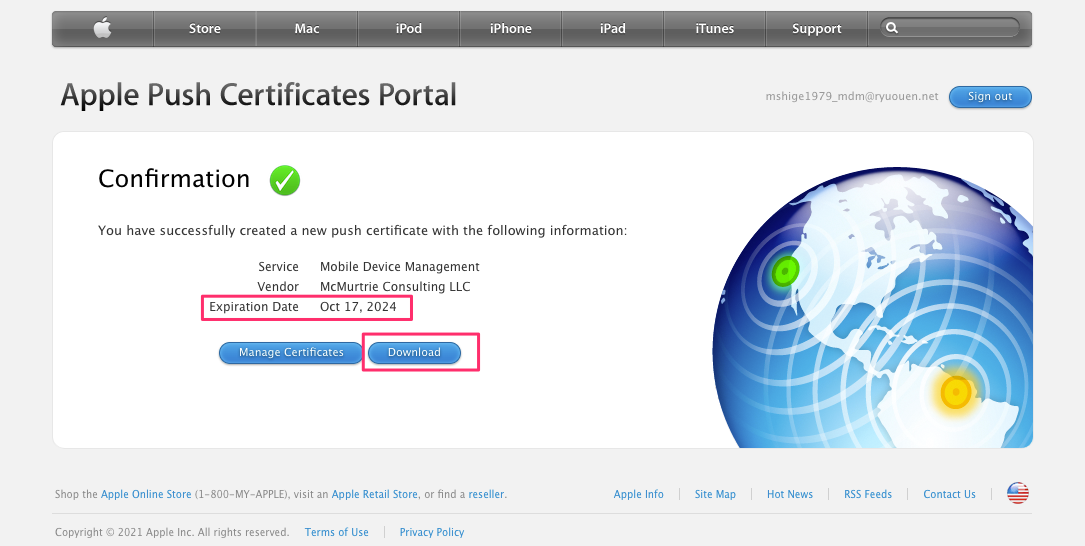
EC2へ配備
mv "MDM_ McMurtrie Consulting LLC_Certificate.cer" MDM_McMurtrie_Consulting_LLC_Certificate.cer scp MDM_McMurtrie_Consulting_LLC_Certificate.cer ec2-user@hogehoge(ホスト名またはIP):~/micromdm/micromdm-1.10.1/.
Let's Encrypt
EC2のポート解放
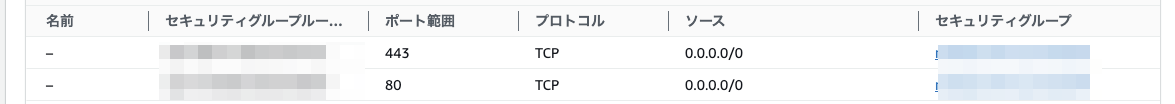
パッケージインストール
sudo yum update -y sudo amazon-linux-extras install -y epel sudo yum install certbot -y
発行
sudo certbot certonly --standalone -d mdm.ryuouen.link -m mshige1979_mdm@ryuouen.net --agree-tos -n
↓
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator standalone, Installer None Requesting a certificate for mdm.ryuouen.link Performing the following challenges: http-01 challenge for mdm.ryuouen.link Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/mdm.ryuouen.link/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/mdm.ryuouen.link/privkey.pem Your certificate will expire on 2024-01-16. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le #
確認
# tree /etc/letsencrypt/live/mdm.ryuouen.link/ /etc/letsencrypt/live/mdm.ryuouen.link/ ├── README ├── cert.pem -> ../../archive/mdm.ryuouen.link/cert1.pem ├── chain.pem -> ../../archive/mdm.ryuouen.link/chain1.pem ├── fullchain.pem -> ../../archive/mdm.ryuouen.link/fullchain1.pem └── privkey.pem -> ../../archive/mdm.ryuouen.link/privkey1.pem 0 directories, 5 files #
MDMサーバ
起動
sudo build/linux/micromdm serve \ -server-url=https://mdm.ryuouen.link \ -api-key hogehoge \ -filerepo /home/ec2-user/micromdm/micromdm-1.10.1 \ -tls-cert /etc/letsencrypt/live/mdm.ryuouen.link/fullchain.pem \ -tls-key /etc/letsencrypt/live/mdm.ryuouen.link/privkey.pem
↓
component=main msg=started level=debug component=depsync msg="loaded DEP config" cursor= level=info msg="serving HTTPS using provided certificates" addr=:https ts="2023/10/18 14:04:29" msg="push: waiting for push certificate before enabling APNS service provider" level=info component=depsync msg="waiting for DEP token to be added before starting sync"
↓

config設定
sudo build/linux/mdmctl config set -name develop -api-token hogehoge -server-url https://mdm.ryuouen.link sudo build/linux/mdmctl config switch -name develop
アップロード
sudo build/linux/mdmctl mdmcert upload \ -cert="MDM_McMurtrie_Consulting_LLC_Certificate.cer" \ -private-key="mdmcert.download.push.key"
プロファイルインストール

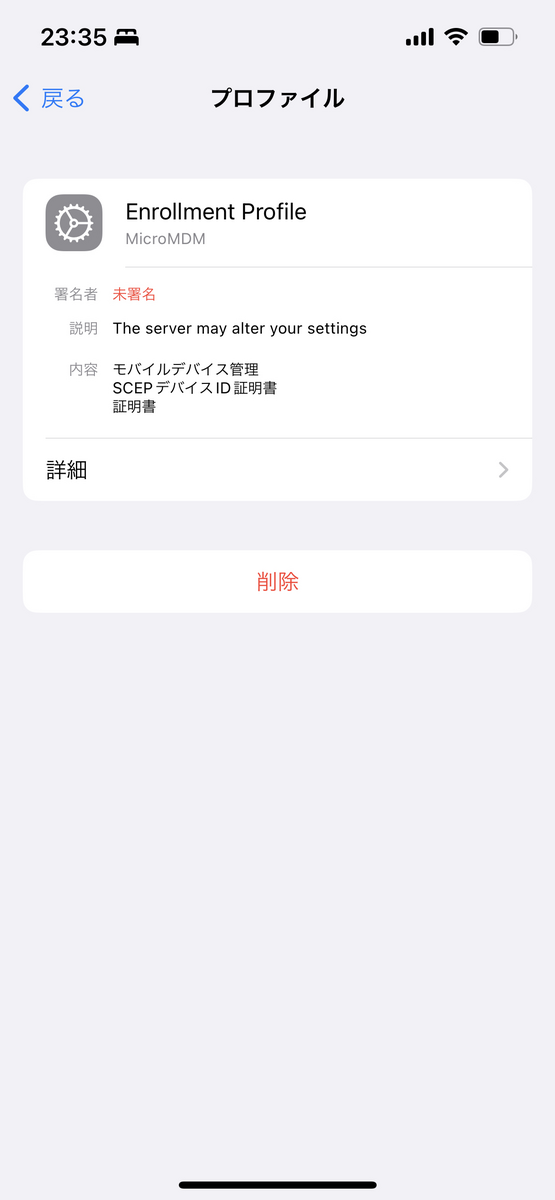
↓
コマンド実行
登録プロファイルを取得
sudo build/linux/mdmctl get devices
↓
$ sudo build/linux/mdmctl get devices UDID SerialNumber EnrollmentStatus LastSeen 00008110-XXXXXXXXXXXXXXXE XXX00000001 true 2023-10-18 14:40:47.030834394 +0000 UTC 00008110-XXXXXXXXXXXXXXXE XXX00000002 true 2023-10-18 14:34:55.834127564 +0000 UTC $
ロックコマンドを実行
curl -i -X POST "https://mdm.ryuouen.link/v1/commands" \
-u "micromdm":"hogehoge" \
-d '{ "request_type": "DeviceLock", "udid": "00008110-XXXXXXXXXXXXXXXE" }'
↓
HTTP/2 201
content-type: application/json; charset=utf-8
strict-transport-security: max-age=63072000; includeSubDomains; preload
content-length: 158
date: Wed, 18 Oct 2023 14:46:08 GMT
{
"payload": {
"command_uuid": "47564d8c-7951-4584-84ed-f5a4339b866c",
"command": {
"request_type": "DeviceLock",
"pin": ""
}
}
}
$
終わり