CAとかわからないけど
ネットで検索していくつか出たものを参考に作成してみた
参考情報
オレだよオレオレ認証局で証明書つくる - Qiita
CentOS7:SSL自己発行局の設置から俺々証明書の作成と承認まで
オレオレ認証局クライアント証明書の作り方(sha256) - Qiita
準備
opensslの設定ファイルをコピー
mkdir -p /etc/pki/caCrt cp -p /etc/pki/tls/openssl.cnf /etc/pki/caCrt/. cp -p /etc/pki/tls/openssl.cnf /etc/pki/caCrt/openssl-ca.cnf cp -p /etc/pki/tls/openssl.cnf /etc/pki/caCrt/openssl-server.cnf cp -p /etc/pki/tls/openssl.cnf /etc/pki/caCrt/openssl-client.cnf
CA用の編集(一部追加)
vi /etc/pki/caCrt/openssl-ca.cnf ---- [ usr_cert ] basicConstraints=CA:TRUE nsCertType = client, email subjectAltName=@alt_names ----
サーバ証明書用の編集(一部追加)
vi /etc/pki/caCrt/openssl-server.cnf ---- [ usr_cert ] basicConstraints = CA:FALSE nsCertType = server subjectAltName=@alt_names ----
クライアント証明書用の編集(一部追加)
vi /etc/pki/caCrt/openssl-client.cnf ---- [ usr_cert ] basicConstraints=CA:FALSE nsCertType = client, email, objsign ----
DNS設定
vi /etc/pki/caCrt/san.txt ---- subjectAltName=DNS:sample.com,DNS:*.sample.com ----
CA(自己認証局)作成
秘密鍵作成
openssl genrsa \
-aes256 \
-out cakey.pem 2048
> Enter pass phrase for cakey.pem: [秘密鍵のパスワード]
> Verifying - Enter pass phrase for cakey.pem: [秘密鍵のパスワード]
CSRファイル生成
openssl req -new \
-config /etc/pki/caCrt/openssl-ca.cnf \
-key cakey.pem \
-out cacert.csr
> Enter pass phrase for cakey.pem: [秘密鍵のパスワード]
> You are about to be asked to enter information that will be incorporated
> into your certificate request.
> What you are about to enter is what is called a Distinguished Name or a DN.
> There are quite a few fields but you can leave some blank
> For some fields there will be a default value,
> If you enter '.', the field will be left blank.
> -----
> Country Name (2 letter code) [XX]:JP ← なんか適当に
> State or Province Name (full name) []:Fukuoka ← なんか適当に
> Locality Name (eg, city) [Default City]:Fukuoka ← なんか適当に
> Organization Name (eg, company) [Default Company Ltd]:OreOre inc. ← なんか適当に
> Organizational Unit Name (eg, section) []: ← ← なんか適当に
> Common Name (eg, your name or your server's hostname) []:localhost ← なんか適当に
> Email Address []: ← ブランク
>
> Please enter the following 'extra' attributes
> to be sent with your certificate request
> A challenge password []: ← ブランク
> An optional company name []: ← ブランク
CA証明書作成
openssl x509 \
-days 3650 \
-in cacert.csr \
-req -signkey cakey.pem \
-out cacert.pem
> Signature ok
> subject=/C=JP/ST=Fukuoka/L=Fukuoka/O=OreOre inc./CN=localhost
> Getting Private key
> Enter pass phrase for cakey.pem: [秘密鍵のパスワード]
認証局管理用のファイルを初期化
touch /etc/pki/CA/index.txt echo 00 > /etc/pki/CA/serial
サーバ証明書
秘密鍵を作成
openssl genrsa -aes256 -out privkey.pem 2048 > Enter pass phrase for privkey.pem: > Verifying - Enter pass phrase for privkey.pem:
CSR作成
openssl req \
-new -key privkey.pem \
-out domain_name.csr
> Enter pass phrase for privkey.pem: [password]
> You are about to be asked to enter information that will be incorporated
> into your certificate request.
> What you are about to enter is what is called a Distinguished Name or a DN.
> There are quite a few fields but you can leave some blank
> For some fields there will be a default value,
> If you enter '.', the field will be left blank.
> -----
> Country Name (2 letter code) [XX]:JP
> State or Province Name (full name) []:Fukuoka
> Locality Name (eg, city) [Default City]:Fukuoka
> Organization Name (eg, company) [Default Company Ltd]:OreOre inc.
> Organizational Unit Name (eg, section) []:
> Common Name (eg, your name or your server's hostname) []:*.sample.com
> Email Address []:
>
> Please enter the following 'extra' attributes
> to be sent with your certificate request
> A challenge password []:
> An optional company name []:
サーバ証明書作成
openssl ca \
-config /etc/pki/caCrt/openssl-server.cnf \
-keyfile cakey.pem -cert cacert.pem \
-in domain_name.csr \
-out domain_name.crt.pem \
-days 825 \
-extfile /etc/pki/caCrt/san.txt
> Using configuration from /etc/pki/tls/openssl.cnf
> Enter pass phrase for cakey.pem:
> Check that the request matches the signature
> Signature ok
> Certificate Details:
> Serial Number: 1 (0x1)
> Validity
> Not Before: Feb 15 04:46:21 2020 GMT
> Not After : May 20 04:46:21 2022 GMT
・
・
・
なんかいろいろでる
クライアント証明書
秘密鍵を作成
openssl genrsa \
-aes256 \
-out client-privatekey.pem 2048
> Enter pass phrase for client-privatekey.pem:
> Verifying - Enter pass phrase for client-privatekey.pem:
CSR発行
openssl req \
-new \
-key client-privatekey.pem \
-out client.csr
> Enter pass phrase for client-privatekey.pem:
> You are about to be asked to enter information that will be incorporated
> into your certificate request.
> What you are about to enter is what is called a Distinguished Name or a DN.
> There are quite a few fields but you can leave some blank
> For some fields there will be a default value,
> If you enter '.', the field will be left blank.
> -----
> Country Name (2 letter code) [XX]:JP
> State or Province Name (full name) []:Fukuoka
> Locality Name (eg, city) [Default City]:Fukuoka
> Organization Name (eg, company) [Default Company Ltd]:OreOre inc.
> Organizational Unit Name (eg, section) []:
> Common Name (eg, your name or your server's hostname) []:OreOre client
> Email Address []:
>
> Please enter the following 'extra' attributes
> to be sent with your certificate request
> A challenge password []:
> An optional company name []:
クライアント証明書作成
openssl ca \
-config /etc/pki/caCrt/openssl-client.cnf \
-cert cacert.pem \
-keyfile cakey.pem \
-out clientcert.crt \
-infiles client.csr
> Using configuration from /etc/pki/caCrt/openssl-client.cnf
> Enter pass phrase for cakey.pem:
> Check that the request matches the signature
> Signature ok
> Certificate Details:
> Serial Number: 2 (0x2)
> Validity
> Not Before: Feb 15 05:08:00 2020 GMT
> Not After : Feb 14 05:08:00 2021 GMT
> Subject:
・
・
なんかいろいろでる
クライアント証明書をpkcs12でエクスポート
openssl pkcs12 \
-export \
-in clientcert.crt \
-inkey client-privatekey.pem \
-out clientcertinbrowser.pfx -name "hogehoge"
> Enter pass phrase for client-privatekey.pem: [password]
> Enter Export Password: [ブランク]
> Verifying - Enter Export Password: [ブランク]
nginx設定
初期設定のものを書き換え
vi /etc/nginx/conf.d/default.conf
----
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
server {
listen 443;
server_name dev.sample.com;
ssl on;
ssl_certificate /vagrant/domain_name.crt.pem;
ssl_certificate_key /vagrant/privkey-nopass.pem;
#charset koi8-r;
#access_log /var/log/nginx/host.access.log main;
location / {
root /usr/share/nginx/html;
index index.html index.htm;
}
}
----↓
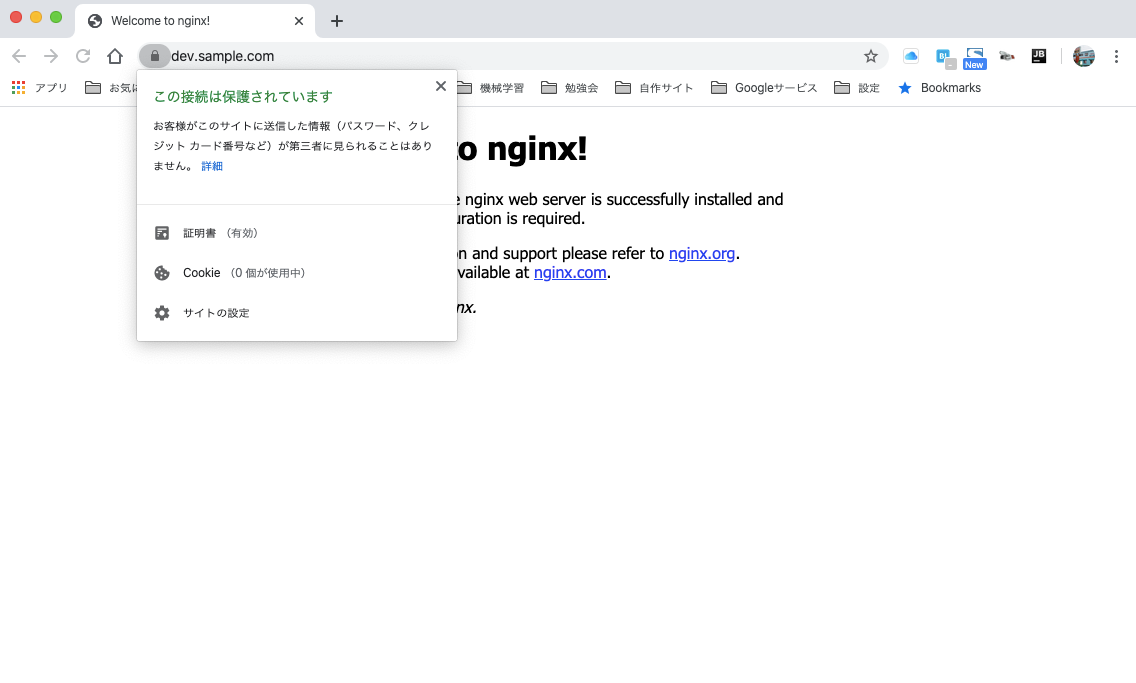
まあ、これでよいかな・・・
■追記
webブラウザで証明書のインポートが別途必要
参考情報
オレだよオレオレ認証局で証明書つくる - Qiita
CentOS7:SSL自己発行局の設置から俺々証明書の作成と承認まで
オレオレ認証局クライアント証明書の作り方(sha256) - Qiita
ありがとうございましたm(_ _)m